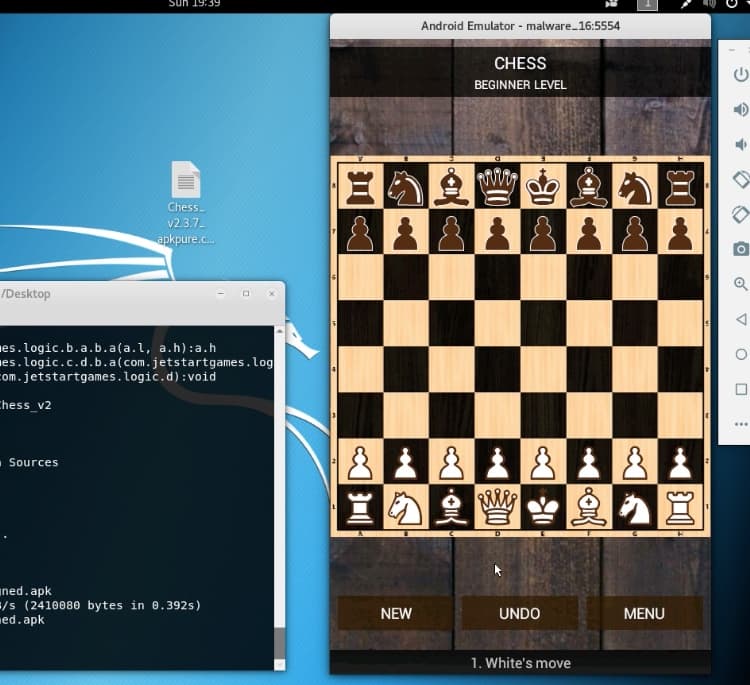
Reverse Engineering and Debugging 3rd Party APKs
As mobile devices continue to become an integral part of our daily lives, the demand for mobile apps and software is also increasing. Mobile app developers work hard to develop and distribute high-quality apps that are user-friendly, secure, and functional. However, not all mobile apps are created equal. Some apps may have hidden security vulnerabilities, bugs, or other issues that can compromise the user's data or device. In this scenario, reverse engineering and debugging third-party APKs becomes essential to identify the problem.
Reverse engineering is the process of breaking down an existing product or system to understand how it works or to create a new product or system that is compatible with it. In the context of mobile apps, reverse engineering involves analyzing the app's code and its behavior to determine its underlying architecture and identify any potential vulnerabilities or bugs. Reverse engineering can also help to gain insights into how the app interacts with other components on the device or with remote servers.
Debugging, on the other hand, is the process of identifying and resolving errors or bugs in software code. Debugging is essential for identifying and fixing issues in mobile apps and ensuring that they function as intended. Debugging can also help to improve app performance, reduce crashes, and improve the user experience.
Why Reverse Engineering and Debugging 3rd Party APKs is Necessary
Reverse engineering and debugging third-party APKs is essential for several reasons. First, it can help to identify any potential security vulnerabilities in the app that could compromise the user's data or device. This is particularly important when dealing with sensitive data, such as financial information, health records, or personal identification information.
Second, reverse engineering and debugging can help to identify and fix any bugs or errors in the app that may be causing crashes, freezes, or other performance issues. This can improve the overall user experience and reduce the likelihood of negative reviews or feedback.
Third, reverse engineering and debugging can help to gain insights into the app's behavior and functionality. This can be useful for developers who are looking to create their own apps or integrate the third-party app's functionality into their own products.
How to Reverse Engineer and Debug 3rd Party APKs
Reverse engineering and debugging third-party APKs can be a challenging task, particularly if the app's code is obfuscated or otherwise protected. However, there are several techniques and tools that can be used to make the process easier and more effective.
- Decompiling the APK: Decompiling the APK file can provide insights into the app's code and architecture. Tools such as apktool can be used to decompile the APK and extract the app's code, resources, and manifest file. Once the APK has been decompiled, the code can be analyzed using tools such as JD-GUI or JADX.
- Analyzing the app's behavior: Once the app has been decompiled, it can be installed on a test device or emulator and its behavior can be analyzed using debugging tools such as Android Studio or Eclipse. This can help to identify any performance issues or bugs in the app's code.
- Using dynamic analysis tools: Dynamic analysis tools, such as Frida, can be used to intercept and modify the app's behavior at runtime. This can be useful for identifying and fixing bugs or for modifying the app's behavior for testing purposes.
- Using static analysis tools: Static analysis tools, such as Androguard or MobSF, can be used to analyze the app's code and identify potential security vulnerabilities or other issues. These tools can also be used to generate reports and visualizations of the app's code and architecture.
- Network traffic analysis: Network traffic analysis can help to identify how the app communicates with remote servers and identify any potential security vulnerabilities or privacy issues. Tools such as Wireshark or Burp Suite can be used to intercept and analyze network traffic from the app.
- Binary analysis: Binary analysis can be used to analyze the app's binary code and identify any potential vulnerabilities or other issues. Tools such as IDA Pro or Ghidra can be used to analyze the app's binary code.
Once the app has been analyzed, any identified issues or vulnerabilities can be addressed by the app developer. However, it is important to note that reverse engineering and debugging third-party APKs can raise legal and ethical concerns. Reverse engineering a commercial app without permission from the app developer can be illegal and may violate copyright laws or software license agreements.
Conclusion
Reverse engineering and debugging third-party APKs is a complex and challenging process, but it can be essential for identifying and resolving security vulnerabilities and other issues in mobile apps. The use of appropriate tools and techniques can help to make the process more effective, but it is important to respect the app developer's intellectual property rights and comply with legal and ethical guidelines when conducting reverse engineering and debugging.
In conclusion, reverse engineering and debugging third-party APKs is an important practice for ensuring that mobile apps are secure, functional, and user-friendly. By using appropriate tools and techniques, app developers can gain valuable insights into the app's behavior and architecture and identify any potential issues that may compromise the user's data or device. However, it is important to conduct reverse engineering and debugging in a legal and ethical manner and respect the app developer's intellectual property rights.