Today we analyze a malicious HTML document that claims the user must download a compatibility plugin in order to view the UPS receipt. This HTML document employs several layers of HTML, Javascript, and Executable obfuscation and we show how to analyze all of them.
Filename
UPS-Receipt-008533234.doc.html
MD5
762B0F20C80995D3AC8A66716011C156
Sample
Video
DETAILS
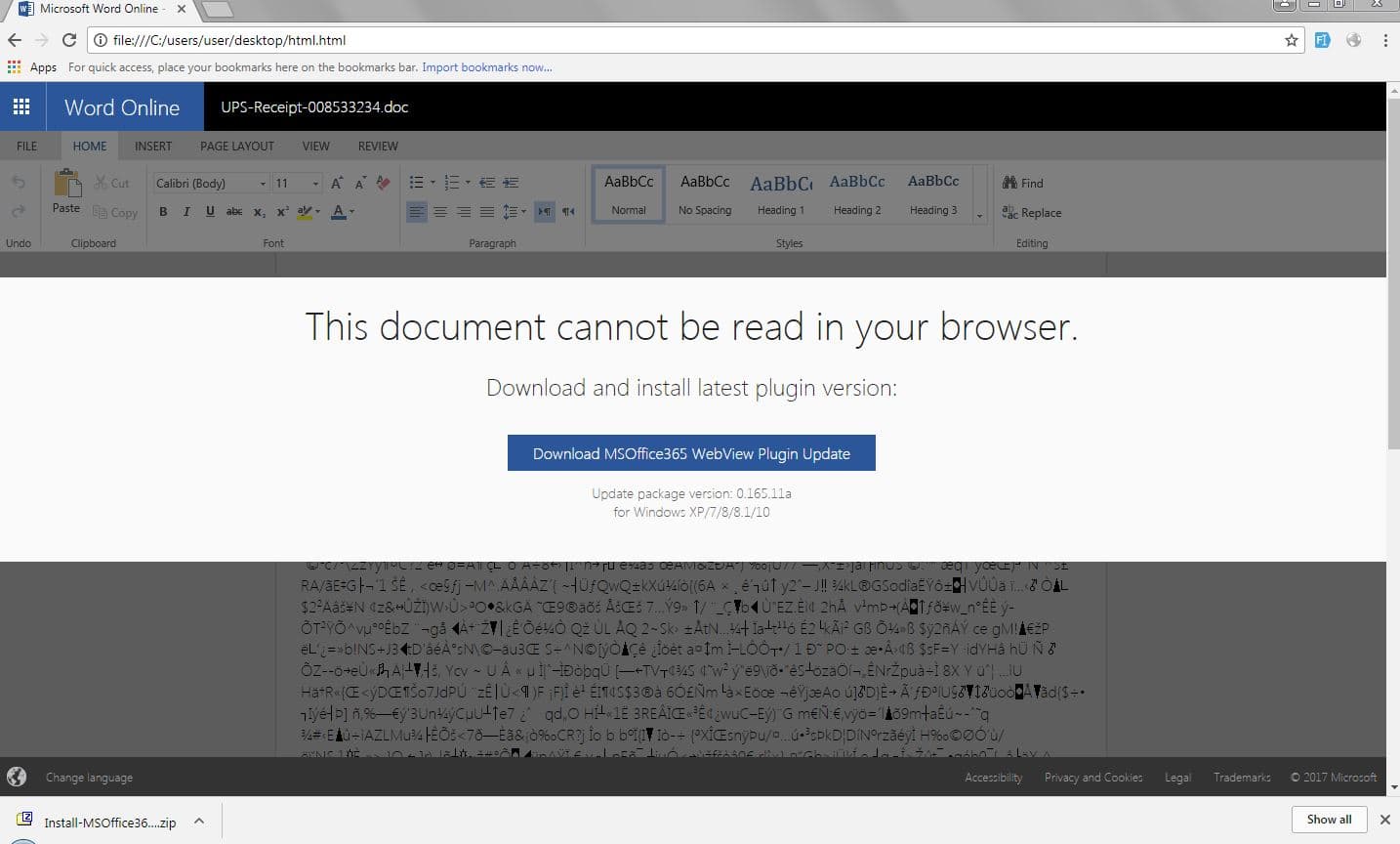
We begin by opening the HTML document and are greeted with a Phishing message claiming that we must download a compatibility plugin in order to view the UPS receipt in Office 365 .
.Inspecting the HTML document reveals that all the components are included in the file via Base64 encoding and it does not rely on any external pictures/resources.
If we click the blue button in the middle of the page to download our "compatibility" plugin, a ZIP is downloaded to our machine (it is not downloaded from an external website, the ZIP is contained within the base HTML.)
Inspecting the ZIP reveals a JavaScript
 file with a name that leads the user to believe it is a compatibility plugin for Office 365
file with a name that leads the user to believe it is a compatibility plugin for Office 365 .
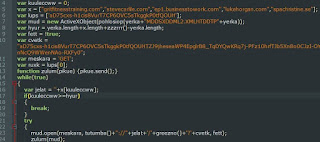
.Diving into the JavaScript reveals decently obfuscated code that aims to download a file from one of 5 separate domains. The domains are contained in an array and are picked via a WHILE loop. The loop will choose the domain to be contacted and append a long string located in the variable "cvetk" to the end of it. This will be the next file downloaded.
The GET request is met with an HTTP
 301 Moved Permanently message:
301 Moved Permanently message:The resulting file downloaded by the 301 Moved Message is another obfuscated JavaScript file. This file has a slightly better obfuscation pattern.
We notice that the file seems to be full of a single appending variable. Formatting this in a text editor reveals the following:
We can format this single string further to get a proper script that can be debugged with WSCRIPT:
Once formatted, the JavaScript
 file can be debugged
file can be debugged by issuing the command wscript.exe //X file.js . Once inside the script, we see that it randomly generates text to place in a dummy Office Document.
by issuing the command wscript.exe //X file.js . Once inside the script, we see that it randomly generates text to place in a dummy Office Document. This Office Document
 is then written to disk and launched as a distraction for the user. It is full of non-legible text generated by the routine described above:
is then written to disk and launched as a distraction for the user. It is full of non-legible text generated by the routine described above:We are finally greeted with the goal of this Phishing attempt; to download a Trojan. We find the following routine in the script which will choose one of five domains and append a long single string variable to it.
If you take the GET request at face value you will be one character short of the actual file being downloaded. You must inspect the nested FOR loops carefully to realize that a one character variable will be appended to the concatenated URL. If the variable is left off, then you will download this second stage script again. You can see the post-pended character in red:
The resulting GET request is for a PNG but is saved as an EXE:
The final file downloaded is a UPX
 packed executable with many detections in VirusTotal. You can unpack this executable with the freely available UPX tool. Even UPX packed, the file is recognized as the popular ransomware Locky:
packed executable with many detections in VirusTotal. You can unpack this executable with the freely available UPX tool. Even UPX packed, the file is recognized as the popular ransomware Locky:DROPPED FILES
Install-MSOffice365-WebView-Plugin-Update-0.165.11a.exe.js[random 9 Character AlphaNumeric name].exe
NETWORK TRAFFIC
http://gritfitnesstraining.com/counter/?aD75cxs-h1cis8VurT7CP6OVC5sTkggkP0tfQOUHTZJ9jheseaWP4EpglrB8_TqDYQwKRq7j-PFz10hrfTJb5Xn8o0CJzI-OYIZKKs5__bDnNcQ9WWenNAo-RXFy0http://amirmanzurescobar.com//counter/?aTZJ9jheseaWP4EpglrB8_TqDYQwKRq7j-PFz10hrfTJb5Xn8o0CJzI-OYIZKKs5__bDnNcQ9WWenNAo-RXFy2
CONCLUSION
Beneath a convincing compatibility plugin HTML page and several layers of obfuscation lay an initial infection vector for the well known Locky ransomware . This has been quite the rabbit hole of obfuscation, but in the end we were able to find good 'ole Locky. Be careful out there. Happy hunting.
. This has been quite the rabbit hole of obfuscation, but in the end we were able to find good 'ole Locky. Be careful out there. Happy hunting.